Student Projects
Projects completed by Interns, Undergraduate, and Masters students associated with the TULIPS lab. Projects very widely and typically represent one summer's amount of work. Resources and publications provided where available and appropriate. Projects are sorted by the year they were completed and then alphabetically by student.
2023
Automatically Generating Contextualised Responses to Phishing Reports
Sean Strain
Supervisors: Kami Vaniea, Adam Jenkins
I propose a novel system that respons to reports of email phishing with contextualised information and advice. The first year of the project analyses a given email for a range of phishing indicators and dynaically generates a set of features that can be used to create a friendly and educational response. The second year of the project involved creating a simulated inbox interface which showed the output of the system in a realistic setting. A study with 22 participants was then used to evaluate how users interacted with the system and how much it helped users identify and learn about phishing.
2022
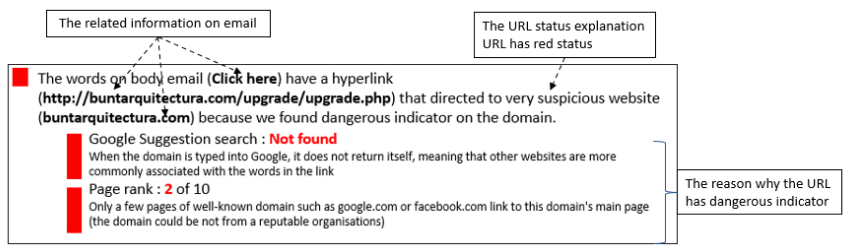
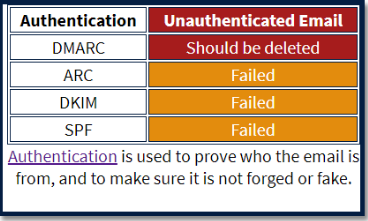
Correlating Information on Email to Help the User Receive Better Understanding on Identifying Phishing Email
Isa Albashar
Supervisor: Kami Vaniea
Phishing is a popular method to obtain sensitive data from users such as login passwords. Unfortunately automatic detection methods, while quite accurate, are not 100%, so some phishing emails appear in user inboxes. Users are recommended to report such email, but they are unlikely to get a quick response if they do. In this project I create a prototype for an auto responder system that gives a summary of email analysis which consists of the email features identified and has a friendly explaination.
BitTrack - Using Game Based Learning to Educate Users on Topics Surrounding the Bitcoin Blockchain
Jahangeer Aslam
Supervisor: Kami Vaniea
Blockchain technology and cryptocurrencies have attracked significant interest both from academia and the public recently. However, despite this interest, the general public has very little understanding of how these technologies actually operate. Game-based learning has been demostrated to be successful in educating people on a variety of topics. This project focuses on teaching users fundamental blockchain concepts using the example of Bitcoin. The goal is to alieviate common misconceptions surrounding Bitcoin's anonymity property. We demonstrate that game based learning is indeed an effective approach for education within this domain.
Cyber Security Game: An education game to teach non-technical employees about phishing emails
Wenning Jiang
Supervisor: Kami Vaniea
Phishing emails are one of the most dangerous attacks in recent years, lurking in email inboxes for the unwary. Serious games present a potential way to teach users about phishing in a more fun environment. This project designed a progressive game where the difficultly raises in levels. Thereby increasing the challenge as the player progresses.
Measure cookie setting behavior of web pages showing cookie privacy warnings
Daniel Kirkman
Supervisor: Kami Vaniea
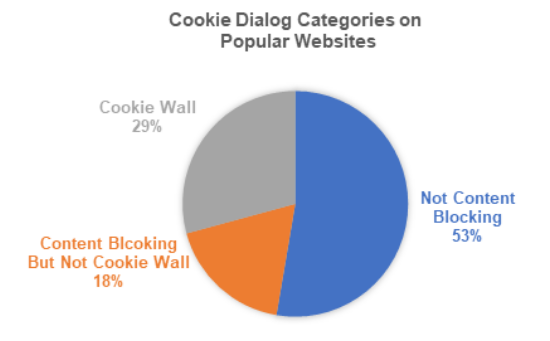
Cookie dialogs are an increasingly common sight across the web but it can still be unclear to users what their true purpose is. These dialogs are intended to allow users to select the level of cookie enablement that matches their personal privacy preferences. However many cookie dialogs use subtle design techniques to nudge users towards accepting more cookies than they need to. These techniques are known as Dark Patterns. In this project I built a tool to automatically detect cookie dialogs and potential dark pattern usage on websites. The reulting system was tested on over 10,000 websites and successfully collected over 2,000 cookie dialogs. It is capable of detecting 10 different types of Dark Pattern and was able to detect over 3,700 instances of Dark Patterns.

Data Hunter: A Cyber Security Game about Web Tracking
Fanwei Meng
Supervisor: Kami Vaniea
Tracking of people's online behaviors is more concerning than ever, especially as awareness increases. Due to a lack of education in the area, few people know how they are bein gtracked online or how to avoid those attacks. This project aimed to use game-based learning to teach users about web tracking. A game called 'Data Hunter' was designed to explain web tracking concepts. Players learn terminology around tracking and anti-tracking.

Analysis of phishing emails for construction of auto-generated advice
Daria Popova
Supervisor: Kami Vaniea
Phishing is an attack that exploits how people interpret email content, in paricular, exploiting: fear of scarcity, authority, guilt, and gullibility. I perform an analysis of an email dataset using deep neural networks and automated classifiers in an effort to provide users with useful predicted guidance.
Measure the Cookie-Setting Behavor of Web Pages Showing Privacy Warnings
Zihan Qiao
Supervisor: Kami Vaniea
After the introduction of regulations like GDPR, it be came necessary for regulators and researchers to be able to track and measure the use of web tracking technologies such as cookies. This project aims to create a platform that enables this type of scientific measurement of cookie dialogs and cookie setting behavior.
Measure the Cookie Setting Behavor of Web Pages Showing Privacy Warnings
Bartosz Strunzinski
Supervisor: Kami Vaniea
Following the introduction of various EU privacy regulations, such as GDPR, many websites started showing cookie privacy warning dialogs to make people aware that the website might be collecting and sharing personal data about them. This project aims to build a tool that can detect these dialogs and determine what happends when a user agrees to the use of cookies (opt-in) and what happens when they choose to disagree (opt-out). The project also looks at a practice called `cookie synchronization' where two trackers synchronize their cookie data with each other thereby making it easier to share personal information about users.
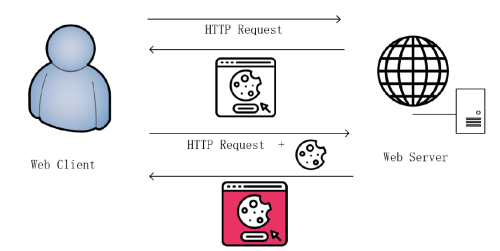
Measure cookie setting behavior of web pages showing cookie privacy warnings
Jim Su
Supervisor: Kami Vaniea
The enactment of GDPR means that the use of tracking technologies like cookies should be limited. They should also be accepted by users before websites set them; however, some websites do not comply with GDPR in different ways such as not displaying options on cookie dialogs. In this project I build a Cookie Dialog Crawler Tool to analyze cookie setting behaviours on different websites. The took can identify and classify cookie dialogs, interact with different options on cookie dialogs, and collect cookies. I analyzed 500 popular websites from the Tranco top visited websites list, and 500 less popular websites from the ParaCrawl list. 54.2% of popular websites displayed a cookie dialog, compared to 17.6% of less popular websites.
2021
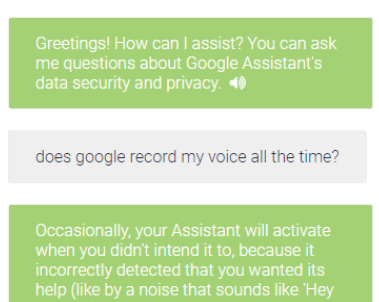
Talk to Google Assistant about Privacy
Nurul Syakirah Binti Ahmad Ghazali
Supervisor: Kami Vaniea
Smart Personal Assistants such as Amazon Echo and Google Home have become prevalent in our daily lives but people still lack the digital literacy and the rights to properly control the information these devices collect and share. One part of the problem is that privacy notices are designed to be read in a written form, but these devices are designed to be interacted with via audio in a queston and answer format. The aim of this project is to explore ways to enable people to interact with the privacy policies of smart personal assitants through their own audio channel. In other words, how do we get Alexa to talk to people about privacy?
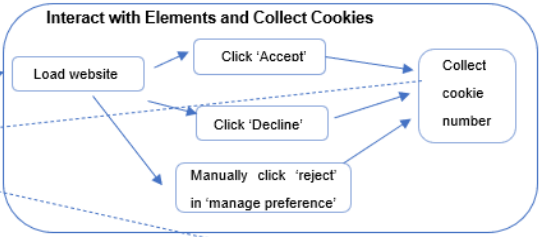
Measure Cookie Setting Behavior of Web Pages Showing Cookie Privacy Warnings
Yiwen Cui
Supervisor: Kami Vaniea
Web cookies are a common form of web tracking technology which fall under the regulation of GDPR leading to the use of cookie consent dialogs on many websites. This project aims to study the content of cookie consent dialogs in relation to some of the requirements of GDPR. The project involved first building a tool to automatically find cookie dialogs and support human labeling for the remainder, then also to automatically find an interact with clickable elements on the dialogs. These tools were used on 958 websites to determine if they were showing a dialog when they set third party cookies, and if they were following GDPR general requirements by giving users meaningful choices.
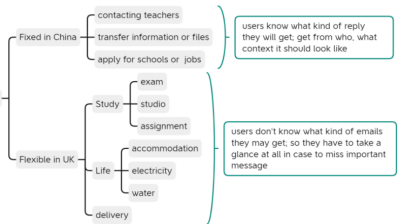
The Impact of Cross-National Differences on Phishing Email Detection Ability
Mingyang Dong
Supervisor: Kami Vaniea
Phishing is a crime that employs both social engineering and technical methods to steal sensitive personal information. People who relocate from a region or culture where communication is done differently can be particularly vulnerable to phishing. One of the most common phishing avoidance advice is to see if the message `looks odd' which is easy for someone who is established in their community or job, but is very challenging for someone who just relocated. This project aims to better understand the phishing-related challenges faced by students who relocated from China to the UK for their studies. We find that University communication in China is normally done over communication channels that verify the sender's identity, like WeChat. Whereas similar communication in the UK is over email which is not properly authenticated. These differences cause challenges for international students.
A Serious Game Designed to Teach Computer Science Students about the Domain Name System
Xuanxuan Du
Supervisor: Kami Vaniea
The Domain Name System (DNS) plays a fundamental role in computer networks, making it relatively easy for people to access websites. However, the principles behind it are often difficult to understand and thus challenging for students to learn. This project’s main goal is to design and build a serious game, which will help computer science students grasp the various kinds of attacks that might occur during the DNS lookup process and its basic concepts.
A Survey on Patching Behaviour of System Administrators
Linsen Liu
Supervisors: Kami Vaniea, Adam Jenkins
How do system administrators decide whether or not to apply a particular patch? How do they prioritise patches? How are these patches tested and deployed? There is no single best answer to these questions, as any number of factors can influence a system administrator’s patching behaviour. In this project, we designed a survey to understand the prevalence of typical patching behaviours of system administrators, and any deviations that may occur in some instances.
Measure the Cookie Setting Behavor of Web Pages Showing Cookie Privacy Warnings
Smilte Petronyte
Supervisor: Kami Vaniea
Websites commonly display cookie privacy warnings to conform to the General Data Protection Regulation (GDPR) and the ePrivacy Directive introduced by the European Union. These regulations require companies to obtain user consent before setting non-essential cookies, such as cookies used for marketing. In this study I performed an emperical analsis of cookie setting behavior and cookies notices found on the top 1000 most visited websites of 2020. I found that approximately 50% of the websites displayed a cookie notice and interacting with the notice usually results in more cookies being set.
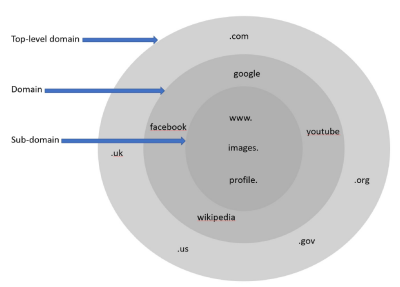
Creating an Educational Resource for Understanding URLs
Ritwik Sarkar
Supervisor: Kami Vaniea
Everyone who has access to the internet has come across a Uniform Resource Locator (URL) at some point. There are millions of different URLs and it is not possible for anyone to know exactly which web page each URL will open but there are standard practices when it comes to the formation of a URL. Despite this, the average user is not usually able to accurately differentiate between a safe URL which will lead them to the site they wish to go to and a malicious one that will redirect them to a dangerous page. My project teaches individuals the basics of URLs. I do this by creating a singular online resource with a collection of videos made by myself and others that explain how to read a URL and how they help us reach the web pages we want to along with common mistakes to look out for.
Measuring Cookie Behaviours Under Different Browser Configurations
Xu Zhang
Supervisor: Kami Vaniea
Cookies play a vital role in the web by offering convenience, but they are still easily exploited by advertising companies. Even though many people do not fully understand how cookies and online-tracking work, they may have installed ad blocker plugins, naively believing that they can protect privacy. In this research, I have implemented a command-line tool for collecting cookie-related data and used it to investigate the effectiveness of many commonly used adblockers and other potentially cookie-blocking solutions. The results were no surprise that some of the most widely used adblockers do not offer the protection that most people believe.
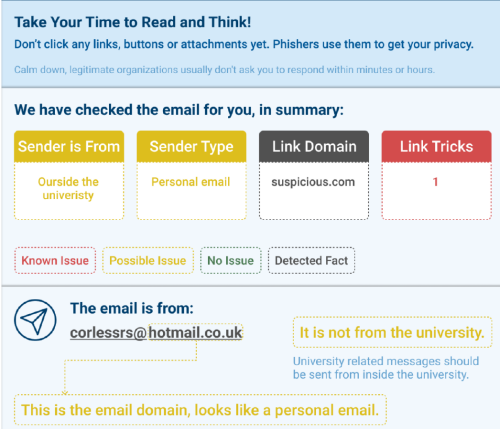
Designing an Autoresponder for Phishing Email Reports
Zeyu Zhang
Supervisor: Kami Vaniea
Nowadays, it is common for organizations to support their members recognizing phishing by encouraging them to report any suspicious emails. However, as a kind of human assistance, not every inquirer can be responded in minutes, while speed can matter a lot because phishers often press their targets to make immediate decisions by injecting a sense of urgency. In addition, as the help desk workers might not be phishing experts either, their feedback is not always helpful that it might be very general but not customized to a certain reported email. Therefore, I designed an automatic responder for phishing email reports, which is technical feasible to implement to return immediate feedback to the inquirer. According to the design, the responder can automatically parse the reported emails and notify the findings through specific colors and texts, ranging from safe to dangerous. This solution combines the human autonomous decision and more reliable automated detection methods, which cover a wider range of phishing features compared to most user-support tools, including email headers, internal URLs, and email body. Also it focuses on explaining those features to ordinary users. Through user evaluation with 6 non-experts participants, the feedback is demonstrated to be generally comprehensible, helpful and friendly.
An Informational Website for Supporting Students and Researchers Doing Ethics
Ningyu Zhao
Supervisor: Kami Vaniea
Although data scientists are proficient in data set processing and analysis, they may lack an ethical understanding, which may trigger potential loopholes in the research process. This project focuses on the ethical issues in the scope of the school of informatics at the University of Edinburgh and analyzes the pain points of students when filling in Participant Information Sheet and making ethics applications and finally give the response to the design opportunities. The final website is designed to help students write Participant Information Sheet in a good manner and assist them to get ethical approval after the first attempt, it also aims to improve the awareness of data protection in a pedagogical setting and help students engaged in data scientist work in the future.
2020
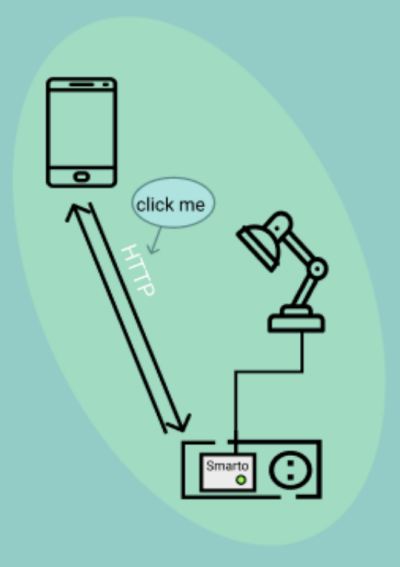
Analysis of Network Traffic to Create an Educational Visualisation of the IoT Ecosystem
Anna Aloshine
Supervisors: Kami Vaniea, Nicole Meng
Assist the general public in understanding how IoT devices communicate within the home by using visualizations; particularly how they interact with other devices such as phones, routers and hubs like Alexa. The project collected packets from a real IoT device and then used the real packet flows to generate a set of scenarios and visualizations that walk a user through what the device is doing.
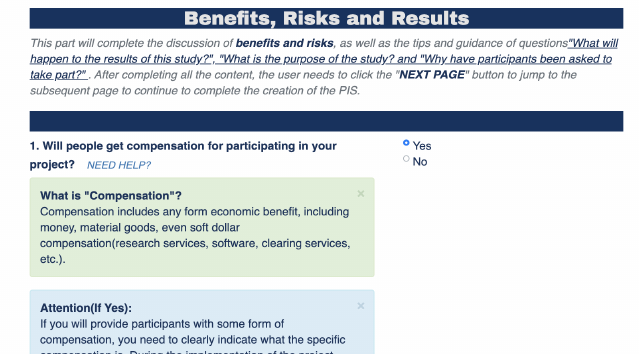
Help Researchers Write Participant Information Sheets for Studies with Humans
Souven Chen
Supervisor: Kami Vaniea
When conducting studies involving human participants, researchers need to make sure participants are informed about the content, risks, and benefits of the study so that participants can make informed choices. However, writing such an information sheet is not necessarily easy for younger researchers, students, or those who have not previously had to direclty work with human participants. In this project, we studied MSc student researchers and built a website tool that would walk them through the process of writing a participant information sheet.
Clustering Phishing Emails to Help the Helpdesk
George Gilligan
Supervisors: Kami Vaniea, Kholoud Althobaiti
In this project I unpack, decode, parse, vectorise and cluster malicious emails, with the intention of grouping them into phishing campaigns. The work is motivated by a desire to automate the work of an organisation helpdesk, who are currently consigned to manual labeling of each phishing email individually. The results show promise that phishing campaings can be clustered.
Build a test platform for HCI Coursework 1
Edward (Xin) Gui
Supervisor: Kami Vaniea
In the Human-Computer Interaction course of the School of Informatics, students build user interface mockups. Building good mockups without feedback is challenging so the purpose of this project is to allow students to get more feedback from their peers. We developed a website to allow students to conduct usability evaluation tests online and get sufficient feedback in a short time through peer evaluation.
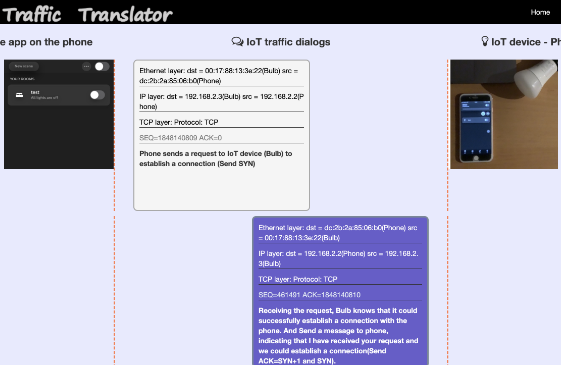
Visualize IoT network traffic as a chat conversation
Luqi Li
Supervisor: Kami Vaniea
IoT network traffic can be challenging for people to understand easily or even learn about. In this project we created a website that allows users to upload a network traffic trace file and then view elements of the file using a more user-friendly chat-themed visualization. The website also featured user training and explainations around common network protocols like TCP.

Measuring the Cookie-Setting Behaviour of Web Pages Showing Privacy Warnings
Barnabas Molnar
Supervisor: Kami Vaniea
Since the introduction of the GDPR within the European Union, the general web browsing experience for millions of people has changed substantially. A considerable portion of websites have been prompting users to agree to the use of technologies, predominantly cookies, which are aimed to track online behaviour and collect personal data. These prompts are most commonly in the form of privacy dialogs, also known as cookie dialogs. The aim of this study was to develop a research platform, which enables researchers to conduct measurements related to these cookie dialogs. The developed platform, called Cookie Dialog Analysier (CDA), facilitates such measurements to provide an understanding on what effects interactions with these dialogs have in terms of newly placed or removed cookies along with many more useful insights.
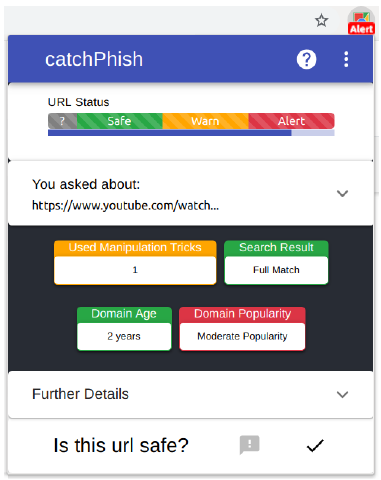
CatchPhish: A URL and Anti-Phishing Research Platform
Stephen Waddell
Supervisors: Kami Vaniea, Kholoud Althobaiti
CatchPhish Phishing Learning and Detection Tool is a browser extension and cloud analysis system designed to improve phishing detection by training users to detect malicious URLs. This work represents a novel contribution to anti-phishing research by combining both passive indicators and active warnings into a system which actively aims to train users.
By leveraging Google cloud technologies, a URL analysis server supports the extension with the ability to scalably analyse URLs with a high degree of accuracy. It is built with a Microservices-based architecture deployed on Google App Engine, which integrates a heuristic algorithm with numerous data sources and 46 distinct heuristics, to facilitate the system's analysis requirements.
The research is underpinned by user studies to gather requirements about what solutions would most benefit users. The evaluation of the overall system illustrates the utility of CatchPhish as a versatile research platform for experimenting with different anti-phishing approaches.
2019

Vulcan - Firewall Administration Game
Rusab Asher
Supervisor: Kami Vaniea
Firewalls play a fundamental role in Computer Security, but configuring the rules for them may prove challenging to beginners in Computer Security. Vulcan intends to help teach informatics students about different ways firewalls can be configured according to different situations using 'iptables'.
Why don't admins patch their systems? Analysis of an email list archive
Pieris Kalligeros
Supervisors: Kami Vaniea, Adam Jenkins
Regular application of patches (updates) is vital to the health of computer systems, but many system administrators either patch slowly or not at all. In this project, we looked at a mailing list archive where system administrators share advice about patching. The project involved building tools to automaticall download and parse the corpus, as well as qualitative coding approaches to understand the meaning of the content.
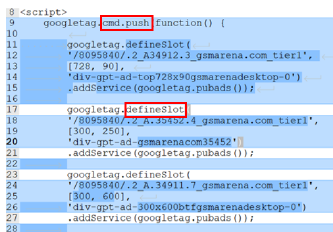
Measure how third-party domain connections change across multiple re-loadings of web pages
Yi Liu
Supervisor: Kami Vaniea
First-party websites are usually dynamically connected with third party domains in order to obtain resources such as images, content, and advertisements. This project aims to help privacy makers, researchers and users better understand what privacy-related choices first-party websites are making. To do so, I designed a system to collect traffic information from the top 100 most popular websites and a random selection of 100 popular websites. I measured the connections of each page to third-party websites over several weeks. I found that websites do change which third-party sites they connect to. Websites in the top 100 most popular change their set of third-party websites less often than the less popular websites.
Use LDA and AutoNER to analyze and automatically extract patch issues
Jiaming Lyu
Supervisor: Kami Vaniea
Keeping systems up to date and patched is a challenging job for a system administrator. While installing patches quickly is good for security, not all patches are safe to install as they may break important parts of the system. In this project, I propose a combinative method of using heuristics and Latent Dirichlet Allocation to identify which patches being discussed on a forum are safe to install and which patches have problems.
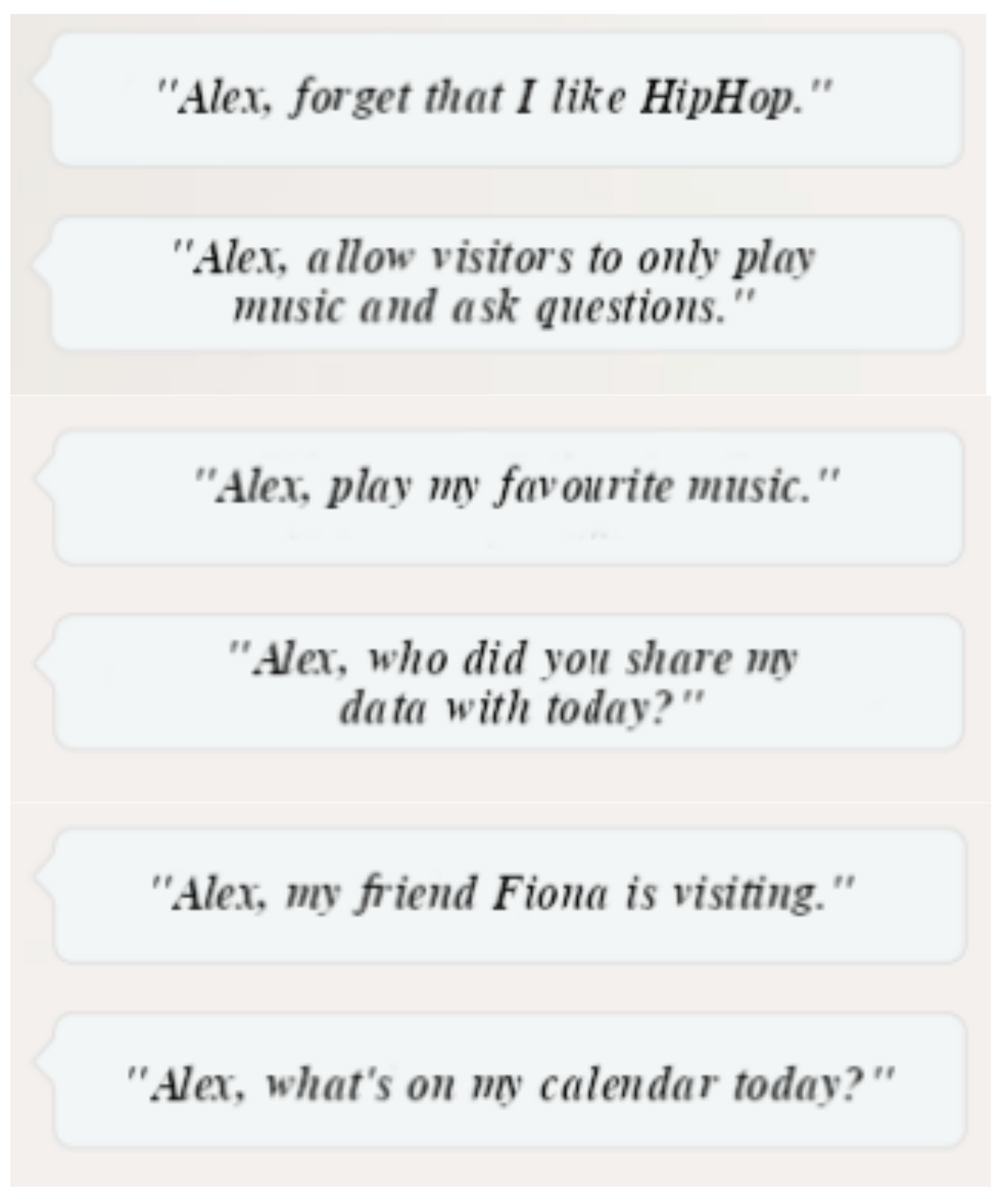
Of Smart Speakers and Men - An Exploration of Privacy and Security Perceptions of Smart Speaker Users in Shared Spaces
Nicole Meng
Supervisors: Kami Vaniea, Bettina Nissen
Smart speakers increasingly adopted into our everyday life. Sometimes, they are also placed in shared spaces and automatically turn every person in the room into a user (visitor) even if they do not regularly interact with it. Previous work primarily focuses on smart speaker adoption and owners, but does not consider the implications of smart speakers on visitors. Our research aims to determine differences between owners and visitors in mental and threat models, privacy perceptions, protection strategies, factors of discomfort. Also, we want to identify which areas of smart speakers need to be addressed to improve smart speaker interactions for both owners and visitors.
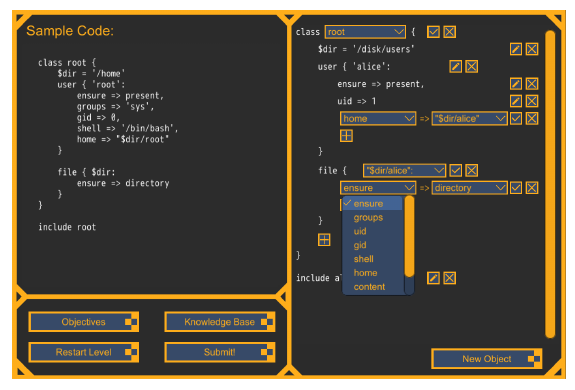
PuppEzy: A Game Based Puppet Programming Teaching Tool
Jaka Mohorko
Supervisor: Kami Vaniea
Many tools used in system administration are often held back by steep learning curves while lacking instructions on how they are to be used. PuppEzy teaches its users how to use one of such tools called Puppet - a configuration management tool. It guides users through the basics of Puppet and teaches them various aspects of the Puppet programming language.
Analysing Online Anti-Fraud Advice to Identify Common Anti-Phishing Instructions and Assumptions
Mattia Mossano
Supervisor: Kami Vaniea
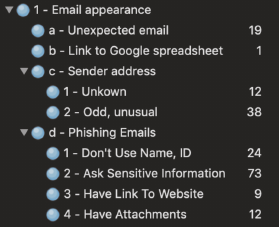
There is a wide variety of anti-phishing advice available through many organizations such as banks, universities, law enforcement, and consumer advacacy groups. In this work, I collect advice from 94 web pages across 9 countries. I find that the advice given to users is disorganized with different advice given by different groups and sometimes the same group offering different advice for differenty entities.
Use forum posts to detect which updates are experiencing problems
Qingyue Zhu
Supervisor: Kami Vaniea
Patching systems quickly can fix system bugs and prevent security issues, however, it may also create new bugs and issues. In this work, I provide patch-issue information at the post level, stentence level, and feature level. My aim is to identify parts of forum posts that discuss patch issues to enable system adminstrators to quicly review only the information important to them and their system. To accomplish this I, used keyword lists to identify posts discussing problems and sentiment analysis to find sentences that express negative sentiment.
2018
Designing a tool to teach password security to future developers
Constance Crowe
Supervisor: Kami Vaniea
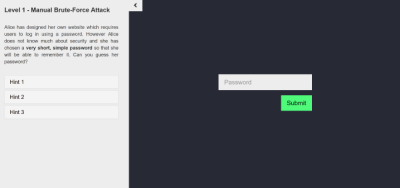
Interactive tutorial that allows people to try out some basic password cracking techniques. My project teaches programmers how to break into a "secure" site by attacking the password, I demonstrate potential vulnerabilities from an attacker's point of view as well as how they can be solved from the defender's perspective.
A Usability Evaluation and Re-design of the password manager software KeePass2
Harris Flourentzos
Supervisor: Kami Vaniea
Explored the usability flaws of a password manager application called KeePass2 when used by the average user. Once the usability issues were discovered, a revised version of the software was developed and tested to provide a more usable alternative to the average user population. The revised version was able to remedy many of the discovered usability issues of the original version. However similar to the original, it had some trouble inducing the correct mental model to the users.

Usability Analysis and Improvement of Two Cryptographic Prototyping Frameworks
Ma Qing Gao
Supervisor: Markulf Kohlweiss
Cryptography schemes can be the core solution for ensuring computer security. This project focuses on conducting two usability lab study to evaluate the usability of two existing. This project focuses on conducting two usability lab study to evaluate the usability of two existing cryptographic prototyping frameworks, which are the three existing Python cryptography programming libraries: Charm, Petlib and Bplib. The final outcomes of this thesis were: (1) giving the weakness and improvement suggestion of the documentation and error respond of these libraries. (2) identify the syntax of which library is more acceptable and understandable by cryptographers.
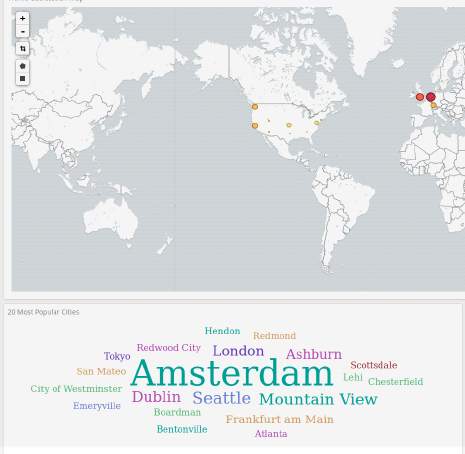
Visualisation of networking connections traversing a single router
Nicholas Lynch
Supervisor: Kami Vaniea
Interactive demo that allows users to visualize their web traffic live. Users connect their personal mobile device to a special Wifi node and see their traffic displayed on a large demo screen. The goal of the project is to facilitate conversations around privacy, security, networking, and what computer scientists do.

A Key to Your Heart: Biometric Authentication Based on ECG Signals
Nikita Samarin
Supervisor: Don Sannella
Over the recent years, there has been a shift of interest towards the field of biometric authentication, which proves the identity of the user using their biological characteristics. In this project, I investigate a biometric based on the electrical activity of the human heart in the form of electrocardiogram (ECG) signals. In order to evaluate the usability and stability of ECG-based biometrics, I perform data collection, signal processing and ECG trace classification.

Web-based tool for estimating security training approaches for security decision-makers
Nan Sheng
Supervisor: Kami Vaniea
Cyber security has been a concern for organizations because it can lead to large financial loss. The premise of this project is that the CISO realizes the improtance of cyber security training and is trying to find a suitable training approach for the staff. This project collects essential information about training approaches from academic papers and training companies such as methodology, charateristic, effectiveness, cost and commercial training products. The goal is to help someone like a CISO select a suitable training approache for the staff.
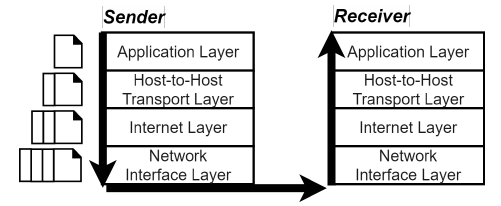
Putting the 'S' in HTTPS: Automatically Fixing Insecure HTTP and Flawed HTTPS Connections in Android
Vesko Stefanov
Supervisor: Kami Vaniea
Cryptographic solutions like HTTPS protect information in transit, but only if they are used correctly by developers. In this project, I develop an early prototype of an Android application which checks all outgoing connections from the device and where possible auto-upgrades them to HTTPS connections. I also test how feasible it is to auto-upgrade HTTP connections in terms of the ability of remote servers to accept the upgraded connections.
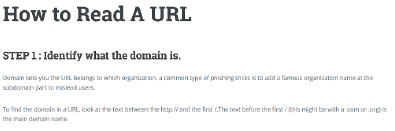
Empirical Evaluation of Users' Ability to Read URLs With and Without a Support Website
Xinding Wang
Supervisor: Kami Vaniea
Reading a URL unaided is challenging. This project had two goals:
1) Determine if people in China and Europe read URLs differently.
2) Build a website that parses and explains a URL to someone in both English and Chinese.

User Studies on Bitcoin Hardware Wallets
Filipe Wang
Supervisors: Myrto Arapinis, Kami Vaniea
The popularity of cryptocurrencies grows by the day. In order to use the different cryptocurrencies, users need to create "wallets" to manage their funds. In this project, we take a look at the most secure type of wallets, hardware wallets, and showcase the results of user studies testing whether users are using the wallets correctly in face of a simulated attack.
2017
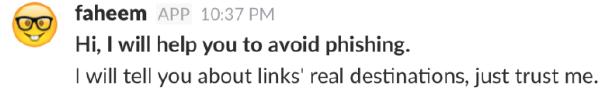
Faheem: Real-time Slack Bot URL Explainer Assists Users in Overcoming Phishing
Kholoud Althobaiti
Supervisors: Stuart Anderson, Kami Vaniea
People have difficulty understanding URLs which makes it harder for them to decide what links are safe to click on or identify potential privacy issues. Faheem is a Slack chat bot designed to help users understand a URL through an interactive discussion with the bot.
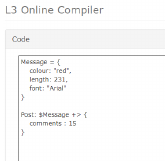
Usability of Configuration Languages: Online Compiler
Aldo Javier Martinez Bacha
Supervisor: Kami Vaniea
Testing the usability of configuration languages as part of a survey is challenging because of the diversity of different languages and the lack of an online compiler to show feedback. In this project, I built an online survey tool where a reseracher can setup a set of tasks and the survey taker can interact and compile their answers in several common configuration languages like L3 and Puppet.
Geolocation Inference on Twitter
Alexander Caughey
Supervisors: Kami Vaniea, Liane Guillou
Machine learning systems were developed to predict the location of origin of a tweet to city-level accuracy. Initially, a state-of-the-art neural network system was re-implemented which achieved comparable results. Subsequently, this system was extended to include more features and extra hidden layers resulting in an increase in successful predictions. Additionally, the hyperparameters of the system were optimised and an ablation test was performed on the system's input features to determine the most beneficial inputs. Design requirements for a defensive privacy-protecting plug-in like tool were acquired in a focus group study. This system could be used to raise social media users' awareness of the impact of machine learning using publicly available data on privacy.

Firewall administration, the game
Ying-An (Annie) Chen
Supervisors: William Waites, Kami Vaniea
Board game focused on configuration of Firewall rules. Computer security is becoming increasingly important in system administration. For this thesis I focused on firewalls as they are a common component of security management. I built a board game which is engaging and motivates people to learn more about Firewalls.

Interactive physical visual aid to support active learning in understanding DDoS concepts
Willy Halim Dinata
Supervisor: Kami Vaniea
This project explored a new way to bring security awareness of Distributed Denial of Service (DDoS) attacks to the masses. The project consisted of a physical-visual aid showing participants a set of simulated Internet of Things (IoT) devices. Participants could interact with the IoT devices through a Facebook chat bot and use them to attack the video server in the center of the board. When all four IoT devices attack at once the video slows to a crawl.
Encrypt me if you can: Helping developers add Transport Layer Security to Android applications
Dimple Gulrajani
Supervisor: Kami Vaniea
An alarming number of mobile applications on the Google Play store do not encrypt their communications leaving them open to Man In The Middle attacks. This thesis analyzes why this is the case and presents a new tutorial to help developers correctly use TLS.
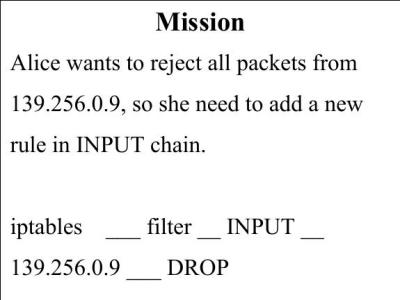
Firewall administration the game
Congcong He
Supervisor: Kami Vaniea
Card game that teaches the IPTables command line to players. During the game players gather Learning cards which teach them about different aspects of IPTables such as chains. They then use the Learning cards to construct IPTables commands to accomplish missions.
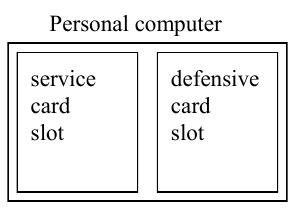
An Educational Game for Computer Security
Yini Huang
Supervisor: Kami Vaniea
Card game where each player must manage a personal computer which hosts services (make money) and defend their network (costs money). Players then try and take down rivals by playing well known attacks against them, and they defend by correctly identifing how to prevent the attack. The game is intended for students who are currently taking a computer security course and want a good way to review common computer security material in a fun way.

Blue Team : A firewall setup game
Karel Kuzmiak
Supervisor: Kami Vaniea
Developed an educational game that can be played in a browser and teaches the basic idea behind firewall administration on a network. The aim of the game is to set up firewall rules in different scenarios, in order to teach the player about iptables syntax, and attack logs from IDS.

Meagle - Crowdsourced software data with community-moderated software reviews
Tom Macmichael
Supervisors: Sebastian Maneth, Kami Vaniea
Finding impartial information about a given piece of software is not easy: there is no single place users can visit to find and contribute information in a consistent manner. This project reated a new website called Meagle, that allows a community of users to review pieces of software with moderation so the best reviews are easy to find.

Firewall simulator as a WebApp
Patrik Mjartan
Supervisors: William Waites, Kami Vaniea
A firewall is a rather straightforward entity at its core - packets trying to get through get inspected and are either let through, or denied. However, configuring and testing a firewall setup can be rather inaccessable to people like students. In particular, setting up multiple machines and VMs can be error prone and problematic for learning. In this project I sought to create a friewall simulator as a WebApp, hence erasing the potentially difficult and time consuming act of setting up the machines.
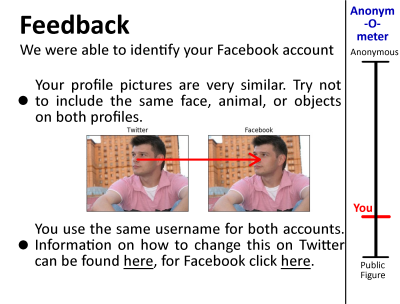
Identifying Social Media Users Across Platforms and Highlighting Privacy Concerns
Timo Mulder
Supervisors: Kami Vaniea, Liane Guillou
The project helps social media users understand that sharing certain types of information online makes it possible for third parties like advertisers and malicious actors to link supposedly anonymous Facebook and Twitter accounts of the same person together. To accomplish this, I conducted a qualitative study to find the design requirements of a feedback system that informs and helps users to avoid online identity resolution. I also examined and successfully developed several approaches to connect social media accounts together.
Building a website for users to rate software updates
Kayode Oduyemi
Supervisors: Sebastian Maneth, Kami Vaniea
End users are not particularly aware of the security implications of not installing updates. This project addresses the problem by creating a website where users can comment on and rate software updates.
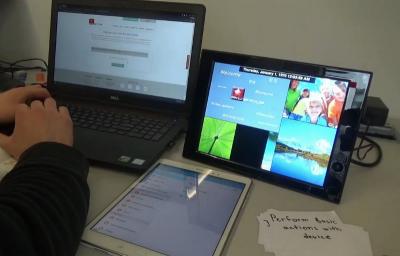
IoT unboxing
Kaloyan Popstoyanov
Supervisor: Kami Vaniea
Developed a systematic process for unboxing IoT devices such that all possible data is captured. I then unboxed 14 devices recording the process from multiple angles, including video of the interactions and packets from both the phone and the IoT device itself.

Permission Impossible - the design and evaluation of a video game that teaches beginners about firewalls
Sibylle Sehl
Supervisor: Kami Vaniea
Certain topics in Computer Security, for example firewalls, can often seem inaccessible or very difficult to beginners. This project aims to bridge this gap by providing an engaging and friendly environment for beginners to learn about firewalls. Permission Impossible teaches novices about basic firewall terminology and concepts as well as how to build a firewall rule set to enable incoming and outgoing packet traffic.

Firewall administration the game
Scott Thompson
Supervisors: Kami Vaniea, William Waites
Managing the Firewall policy rules for a large network is a challenging task, even for a skilled system administrator. Learning these skills can seem insurmountable. In this thesis, I present a Flash game that teaches people how to wirte IPTables rules through a mission-based game.
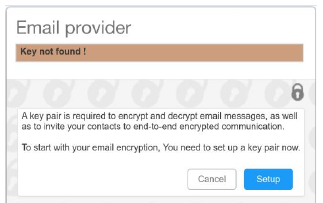
Mailvelope: Evaluate the usability of a security or privacy tool
Qingyu Zhou
Supervisor: Kami Vaniea
To be secure, email encryption solutions also need to be usable. In this project I evaluate the usability of the Mailvelope plugin. I find that many of the issues identified by prior work, such as confusion over public/private keys, remain an issue in Mailvelope. I also propose a new user interface design which is more usable.
2016
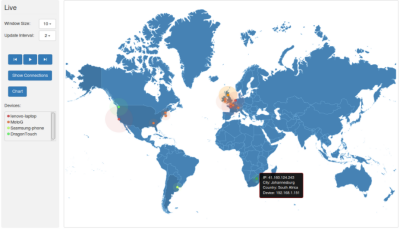
Visualize router traffic
Constantinos Chrysostomou
Supervisor: Kami Vaniea
The Internet of Things (IoT) can make it seem like we have lost control over where our data goes. In this project we took IoT traffic passing across a home network router and visualized where in the world the traffic was going in a live display. The system used D3 for the visualization and a system created by Nikolaos Tsirigotakis to do the packet capture.

Learn Security
Rory Mathers
Supervisor: Don Sannella
Android app for teaching about the following kinds of web security threats, from the OWASP top 10 list: session attacks, SQL injection, cross-site scripting, cross-site request forgery, and sensitive data exposure. It's designed for smartphones; it works on tablets as well but looks better on 7-inch tablets than on large tablets. It's completely self-contained, demonstrating attacks on a simulated bank website, and countermeasures, and requires no permissions to install - there is no danger to your security.
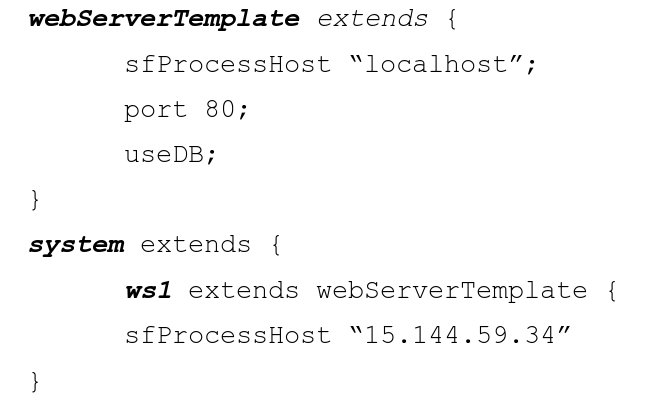
Usability of system configuration langauges: Errors caused by ordering
Adele Mikoliunaite
Supervisors: Paul Anderson, Kami Vaniea
Being a system administrator in todays environment can be quite challenging with a large number of systems to manage and typically minimal formalized training. Configuration languages such as Puppet, SmartFrong, and L3 help administrators manage their large systems but are these languages usable for novices? In this work I administered a survey to look at the intuitive judgements of admins on configuration features such as referencing, inheritance, scope, and ordering. I found that ordering does matterin certain contexts, especially when paired with other features.

Measure the churn of Javascript across multiple re-loadings of web pages
Zhouting Ouyang
Supervisor: Kami Vaniea
When a user visits a webpage the contents of the page is retrieved from various other linked pages. Some of the retrieved content is Javascript which is not owned or hosted by the main site being visited. In this thesis I build a web crawler using Java that measured the number and type of Javascript being retrieved from popular websites. I find that after 10 days around 50% of sites have changed the Javascript being loaded.
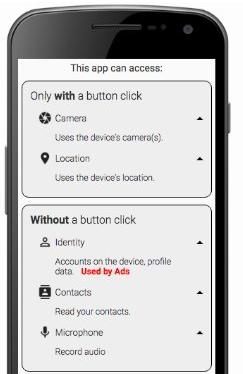
Using static analysis to display privacy properties of apps
Maria Paz Velarde
Supervisor: Kami Vaniea
This project uses static analysis to understand not only what permissions are being used but what an app does with the permissions. We conducted a short user study to identify what types of app permission behaviors worry end users. We found that users care about the contexts in which an app activates permissions. For example, permissions activated with a button press were less concerning than those activated in the background when the app hadn't even been opened. We then created a redesign of the Android permission interface that shows this type of information to the user.
Talking Buses: Transport Planning for Blind and Partially Signted People
Craig Snowden
Supervisor: Kami Vaniea
Using public transportation is a necessity for some blind and partially sighted people, but with accessible information not widely available, accessing these public services can be demotivating. The goal of this project was to implement an iOS mobile application to access public transport information in an accessable manner.
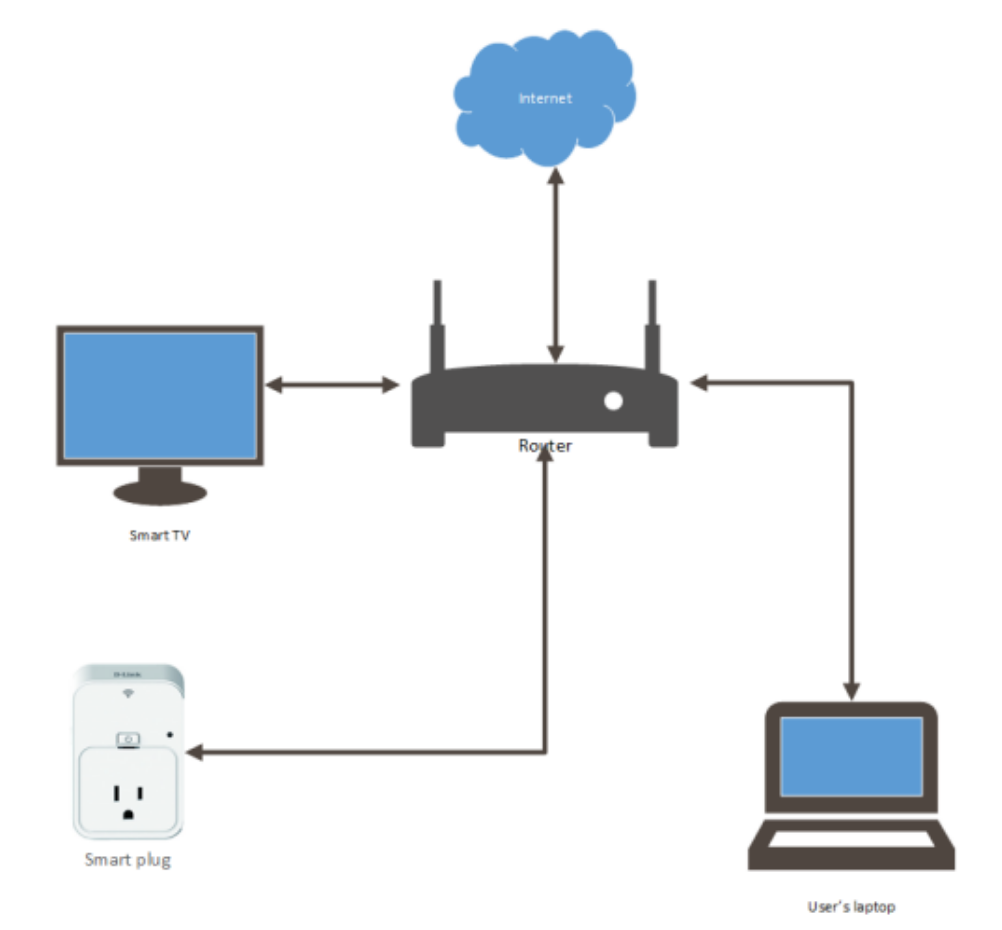
A framework for an en masse network security evaluation and network flow analysis for the Internet of Things era
Nikolaos Tsirigotakis
Supervisor: Kami Vaniea
Internet of Things (IoT) is characterized by rapid expansion on top of several different standards, protocols, and technologies, making security evaluation on a per-devices scale prohibitively time consuming. This project focused on building a router-based platform to change all that by allowing the automation of security checks.

Find conflicting privacy policies on a webpage
Fangkai Wang
Supervisor: Kami Vaniea
When a website loads content from a third-party some information, such as cookies and header data, is also sent to that third party. Both the first and third party websites have their own privacy policies and there is no guarentee that the policies agree with each other. In this thesis I built a privacy policy collector to find privacy policies from both first and third parties. I then use Natural Language Processing to measure similarity as well as measure how long it would take a human to read the policies.
2015

Learn Security
Mac Chong
Supervisor: Don Sannella
Android app for teaching about the following kinds of web security threats, from the OWASP top 10 list: session attacks, SQL injection, cross-site scripting, cross-site request forgery, and sensitive data exposure. It's designed for smartphones; it works on tablets as well but looks better on 7-inch tablets than on large tablets. It's completely self-contained, demonstrating attacks on a simulated bank website, and countermeasures, and requires no permissions to install - there is no danger to your security.
