Security Games
Training new people in cyber security and privacy is a serious issue as we face a global shortage of workers skilled in this area. In this work, we explore the use of gamification to engage people interested in learning about various aspects of cyber security.
Gamification is the process of taking a training exercise or other activity and converting it into a game. Luckily cyber security already has goals which align well with game-type thinking. There is often a resource (computer, system, data) which needs to be protected or attacked. There are also various tools which can be used to perform or defend against those attacks which the player must become familiar with.
In this project we are exploring the use of games to teach security and privacy concepts to all types of students.
Also see:
Publications
- Permission Impossible: Teaching Firewall Configuration in a Game Environment [bibtex]
S. Sehl, K. Vaniea; In Proceedings of the European Workshop on Usable Security (EuroUSEC'18). 2018.
People
CurrentRelated Student Projects
BitTrack - Using Game Based Learning to Educate Users on Topics Surrounding the Bitcoin Blockchain
Jahangeer Aslam
Supervisor: Kami Vaniea
Blockchain technology and cryptocurrencies have attracked significant interest both from academia and the public recently. However, despite this interest, the general public has very little understanding of how these technologies actually operate. Game-based learning has been demostrated to be successful in educating people on a variety of topics. This project focuses on teaching users fundamental blockchain concepts using the example of Bitcoin. The goal is to alieviate common misconceptions surrounding Bitcoin's anonymity property. We demonstrate that game based learning is indeed an effective approach for education within this domain.
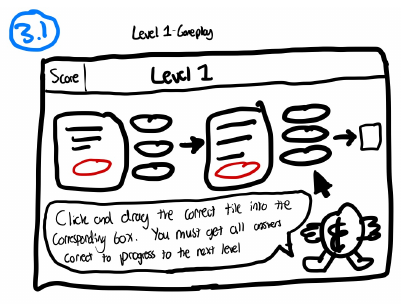
Cyber Security Game: An education game to teach non-technical employees about phishing emails
Wenning Jiang
Supervisor: Kami Vaniea
Phishing emails are one of the most dangerous attacks in recent years, lurking in email inboxes for the unwary. Serious games present a potential way to teach users about phishing in a more fun environment. This project designed a progressive game where the difficultly raises in levels. Thereby increasing the challenge as the player progresses.

Data Hunter: A Cyber Security Game about Web Tracking
Fanwei Meng
Supervisor: Kami Vaniea
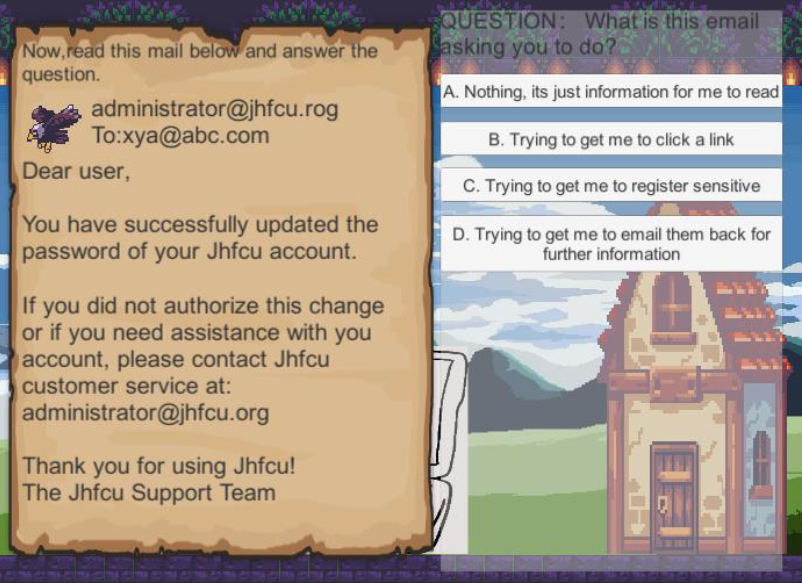
Tracking of people's online behaviors is more concerning than ever, especially as awareness increases. Due to a lack of education in the area, few people know how they are bein gtracked online or how to avoid those attacks. This project aimed to use game-based learning to teach users about web tracking. A game called 'Data Hunter' was designed to explain web tracking concepts. Players learn terminology around tracking and anti-tracking.
A Serious Game Designed to Teach Computer Science Students about the Domain Name System
Xuanxuan Du
Supervisor: Kami Vaniea
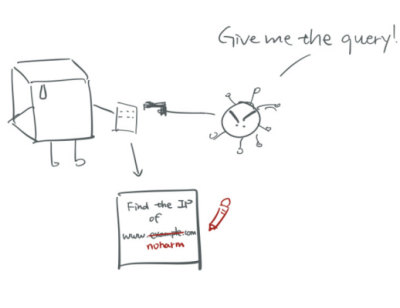
The Domain Name System (DNS) plays a fundamental role in computer networks, making it relatively easy for people to access websites. However, the principles behind it are often difficult to understand and thus challenging for students to learn. This project’s main goal is to design and build a serious game, which will help computer science students grasp the various kinds of attacks that might occur during the DNS lookup process and its basic concepts.

Vulcan - Firewall Administration Game
Rusab Asher
Supervisor: Kami Vaniea
Firewalls play a fundamental role in Computer Security, but configuring the rules for them may prove challenging to beginners in Computer Security. Vulcan intends to help teach informatics students about different ways firewalls can be configured according to different situations using 'iptables'.
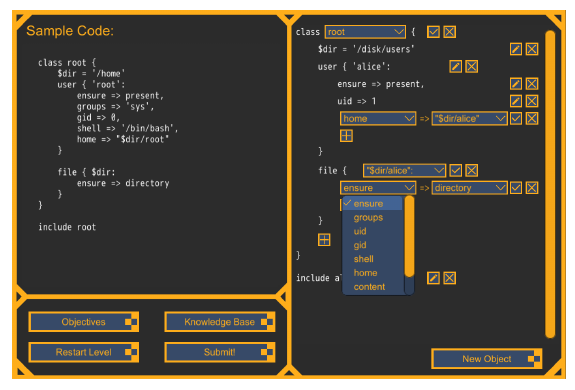
PuppEzy: A Game Based Puppet Programming Teaching Tool
Jaka Mohorko
Supervisor: Kami Vaniea
Many tools used in system administration are often held back by steep learning curves while lacking instructions on how they are to be used. PuppEzy teaches its users how to use one of such tools called Puppet - a configuration management tool. It guides users through the basics of Puppet and teaches them various aspects of the Puppet programming language.
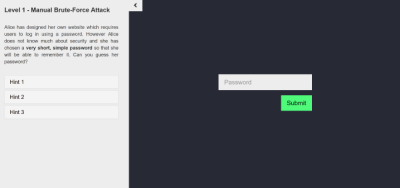
Designing a tool to teach password security to future developers
Constance Crowe
Supervisor: Kami Vaniea
Interactive tutorial that allows people to try out some basic password cracking techniques. My project teaches programmers how to break into a "secure" site by attacking the password, I demonstrate potential vulnerabilities from an attacker's point of view as well as how they can be solved from the defender's perspective.

Firewall administration, the game
Ying-An (Annie) Chen
Supervisors: William Waites, Kami Vaniea
Board game focused on configuration of Firewall rules. Computer security is becoming increasingly important in system administration. For this thesis I focused on firewalls as they are a common component of security management. I built a board game which is engaging and motivates people to learn more about Firewalls.
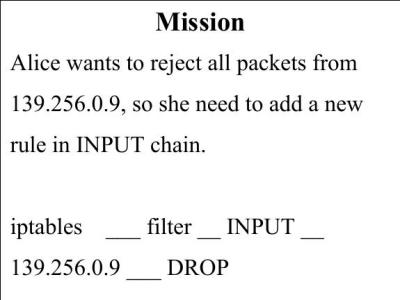
Firewall administration the game
Congcong He
Supervisor: Kami Vaniea
Card game that teaches the IPTables command line to players. During the game players gather Learning cards which teach them about different aspects of IPTables such as chains. They then use the Learning cards to construct IPTables commands to accomplish missions.
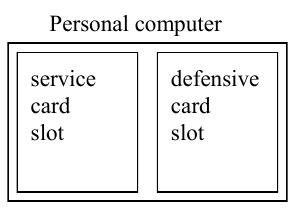
An Educational Game for Computer Security
Yini Huang
Supervisor: Kami Vaniea
Card game where each player must manage a personal computer which hosts services (make money) and defend their network (costs money). Players then try and take down rivals by playing well known attacks against them, and they defend by correctly identifing how to prevent the attack. The game is intended for students who are currently taking a computer security course and want a good way to review common computer security material in a fun way.

Blue Team : A firewall setup game
Karel Kuzmiak
Supervisor: Kami Vaniea
Developed an educational game that can be played in a browser and teaches the basic idea behind firewall administration on a network. The aim of the game is to set up firewall rules in different scenarios, in order to teach the player about iptables syntax, and attack logs from IDS.

Firewall simulator as a WebApp
Patrik Mjartan
Supervisors: William Waites, Kami Vaniea
A firewall is a rather straightforward entity at its core - packets trying to get through get inspected and are either let through, or denied. However, configuring and testing a firewall setup can be rather inaccessable to people like students. In particular, setting up multiple machines and VMs can be error prone and problematic for learning. In this project I sought to create a friewall simulator as a WebApp, hence erasing the potentially difficult and time consuming act of setting up the machines.

Permission Impossible - the design and evaluation of a video game that teaches beginners about firewalls
Sibylle Sehl
Supervisor: Kami Vaniea
Certain topics in Computer Security, for example firewalls, can often seem inaccessible or very difficult to beginners. This project aims to bridge this gap by providing an engaging and friendly environment for beginners to learn about firewalls. Permission Impossible teaches novices about basic firewall terminology and concepts as well as how to build a firewall rule set to enable incoming and outgoing packet traffic.

Firewall administration the game
Scott Thompson
Supervisors: Kami Vaniea, William Waites
Managing the Firewall policy rules for a large network is a challenging task, even for a skilled system administrator. Learning these skills can seem insurmountable. In this thesis, I present a Flash game that teaches people how to wirte IPTables rules through a mission-based game.

Learn Security
Rory Mathers
Supervisor: Don Sannella
Android app for teaching about the following kinds of web security threats, from the OWASP top 10 list: session attacks, SQL injection, cross-site scripting, cross-site request forgery, and sensitive data exposure. It's designed for smartphones; it works on tablets as well but looks better on 7-inch tablets than on large tablets. It's completely self-contained, demonstrating attacks on a simulated bank website, and countermeasures, and requires no permissions to install - there is no danger to your security.

Learn Security
Mac Chong
Supervisor: Don Sannella
Android app for teaching about the following kinds of web security threats, from the OWASP top 10 list: session attacks, SQL injection, cross-site scripting, cross-site request forgery, and sensitive data exposure. It's designed for smartphones; it works on tablets as well but looks better on 7-inch tablets than on large tablets. It's completely self-contained, demonstrating attacks on a simulated bank website, and countermeasures, and requires no permissions to install - there is no danger to your security.
